IT Security Solution & Services
Creative solutions, creative results.
About Us

Our complete line-up of Security enterprise solutions represents the best-of-breed security solutions currently available in the market.
We maintain a high level of professionalism as we continuously ensure our customers acquire the necessary solution and also remarkable service backed with skills and experience from end to end starting from project initiation to implementation, technical training and after sales support and maintenance.
Penetration Testing Services

Cyber security penetration testing provides your company with an opportunity to uncover vulnerabilities that put your main business assets at risk.
Your Business is a/ an:
- Startup
Young startups that work with other businesses are usually asked if a penetration test has been performed since it is important for their clients to analyze and measure the security level of services provided by a startup.
- Midsize company
Midsize companies usually work hard to expand their businesses so whenever a significant change is made to a company's environment, security testing services are reguired security testing servives are reguired.
- Enterprise
Large enterprise companies typically adopt penetration testing program to avoid potential financial and reputational losses in a case of a data breach, which would be enormous or
sometimes even fatal for a business.
In all these cases, software penetration testing is a valuable measure to find security breaches before an attacker can exploit them. Possible examples of the business impact from such an attack could include theft of sensitive information, unauthorized utilization of server resources, or compromise of the company's internal infrastructure using the vulnerable application as a gateway.
What Kind of Penetration Test Do You Need?
Penetration testing is designed to help you assess the effectiveness level of your security teams. We try to identify possible security issues that can lead to the leak of sensitive information or a case when a malicious user, without appropriate permissions, could get access to sensitive information. Our activities fall into one of the following categories:
- Black Box Penetration Testing
This is a classic case of checking a company's security posture by emulating an external attacker who is trying to get unauthorized access to the system. Other activities include attempts to interfere with application users or impact system in another negative way.
- Grey Box Penetration Testing
In This scenario, an engagement that allows a higher level of access and increased internal knowledge is taking place. This test simulates an attacker that has already some knowledge of a company's internals. The attacker is represented as a malicious employee or uses
previously compromised credentials of a legilimate user.
- White Box Penetration Testing
The goal of a white-box test is to extend the number of hidden vulnerabilities and detection rates. Conducting a white box security assessment enables a tester to go deeper and find vulnerabilities in the target environment application source code.
How Neotech Can Help
Neotech's penetration testing experts have conducted dozens of penetration tests for businesses of all sizes across Indonesia.
While automating certain routine checks, our pentest's primary focus is made on manual testing, which helps to identify any remaining issues that can be overlooked by your competitors. All our security analysts have over three years of experience in vulnerability assessment and security and penetration testing projects, and they maintain major security certifications, including OSCP and C|EH.
SOC as A Services
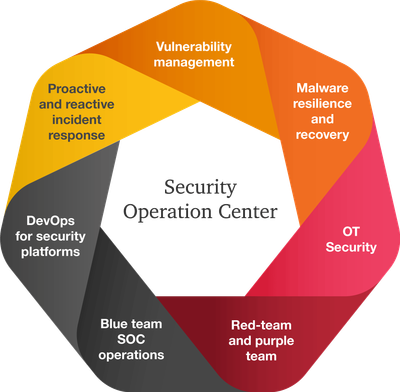
Our SOCaaS delivers all of the benefits of a dedicated 24/7 SOC, but without the high costs, complexity, and frustrations that come with building, staffing, and managing one in-house. With a managed SOC service, organizations are able to outsource the people, processes, and technology needed fora SOC, which is operated and managed offsite and delivered as a cloud based service.
Organizations of all sizes need defenses and expertise that allow them to monitor for threats day and night. SOC-as-a-Service provides an avenue for organizations to gain an end-to-end detection and response solution designed to account for today's SOC challenges and at a manageable price point.
Neotech SOC-as-a-Service provides:
- A modern, cloud-native SaaS platform that accelerates, and improves the effectiveness of, threat detection, hunting, investigation, triaging, case management, and remediation
- Ateam of experts that operate as an extension to your security operations team
- Comprehensive and timely threat intelligence and research
- Incident response services and professionals
- Security device deployment, monitoring and management
- Maturity and repeatability through SLAs, runbooks, and playbooks
- Daily reporting system and ad hoc information trough incident findings
- ISO 27001 certification
Server/System Security

Mictosegmentation For Virtual Server
Micro-segmentation is a network security technique that enables security architects to logically segment a data center into various security segments down to the individual workload level and define security controls to service each individual segment.
Learn More
Virtual Backup and Replication (VBR)
A backup version of a virtual machine can be created on the host where the original VM resides, an adjacent local host, or a host located away from the organization. Computer professionals can configure backup VMs in primary and secondary locations.
Learn MoreData Security

Encryption
Encryption can secure digital data using one or more mathematical techniques known as cryptography.
Learn More
Data Clasification
Data classification is all about understanding and organizing data into defined categories and types that are relevant to a specific organization.
Learn More
Data Loss Prevention
Data Loss Prevention (DLP) is the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data.
Learn More
Data Wiping
Data wiping makes data unreadable, but it does not remove the data. Instead, data wiping is the process of overwriting the data on a particular hard drive to such an extent that the original data is unreadable.
Learn MoreCommunication Security
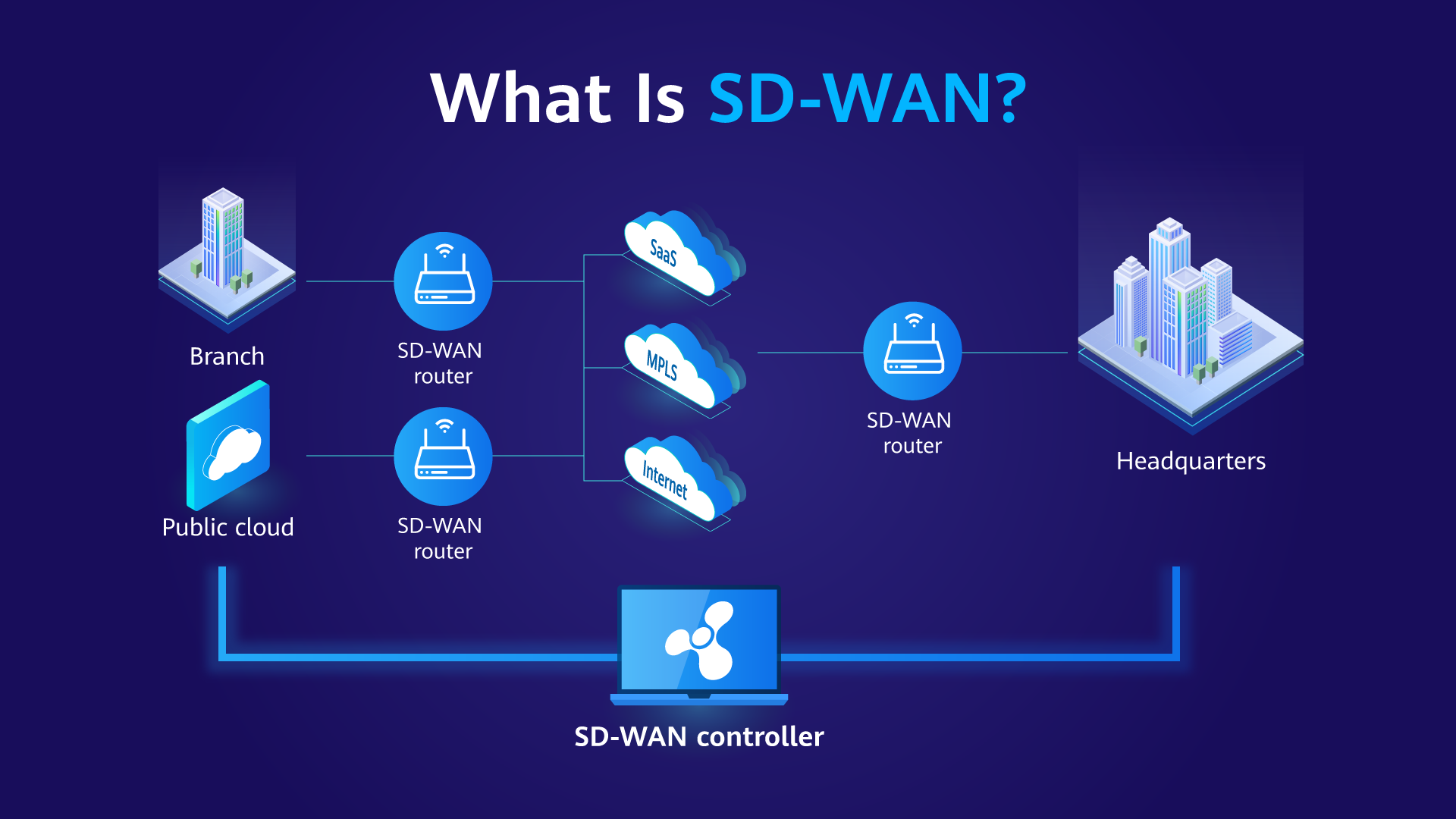
Software-Defined Wide Area Network (SD-WAN)
What Is SD-WAN?
A software-defined wide area network (SD-WAN) implements connectivity between enterprise branches, headquarters, and multiple clouds, allowing applications to scale between hybrid connectivity (including MPLS, Internet, 5G, and LTE connectivity) and high-speed networks. allows you to choose the best link for your data transfer. Quality cloud - service experience. SD-WAN improves the reliability, flexibility and O&M efficiency of enterprise branch networks, keeps branch networks always online, and ensures service continuity and stability.
Enterprise networks are facing issues such as closed WAN architecture, difficult service experience assurance, slow service deployment, and difficult O&M. To address these issues, SD-WAN Solution implements all-scenario and on-demand interconnection between enterprise branches and between enterprise branches and data centers. This solution stands out with the application-based intelligent traffic steering and acceleration as well as intelligent O&M features to deliver better service experience and reshape the full-process service outcomes of enterprise WAN interconnections.
How Is SD-WAN Security Ensured?
The SD-WAN security can be ensured from two aspects: system security and service security. System security is a mandatory, basic security capability of the SD-WAN Solution. After system initialization, the SD-WAN Solution should have capabilities to ensure secure and reliable system running. Service security is ensured by separately deploying flexible security functions based on the service security requirements of enterprises.
- System securitySystem security covers communication security between components in the SD-WAN solution, multi-tenant security, and component security. The SD-WAN Solution consists of multiple components. The components and the communication between them may encounter security threats. Security measures must be taken to ensure the security and reliability of the SD-WAN Solution.
These measures include identity authentication, data encryption, data verification, and permission control, which prevent security issues such as unauthorized access, information leakage, and data tampering. Especially in CPE access scenarios, the SD-WAN Solution strictly verifies CPE identity information based on the Zero-Trust concept. This approach ensures that only authorized and trusted CPEs can access the network, preventing CPE identity spoofing. - Service securityService security involves the security of services carried by the SD-WAN Solution. Based on the service model of an enterprise, service security covers the security of the inter-site access, Internet access, and cloud access services.
To meet service security requirements, proper security measures must be taken for the services. For example, for the inter-site access service, data must be encrypted for secure transmission on the Internet. For the Internet access service, CPEs or uCPEs provide security functions such as ACL-based packet filtering, firewall, intrusion prevention system (IPS), URL filtering, and VAS advanced security functions, preventing various attacks and intrusions.
These security functions can be configured for each VPN. That is, differentiated service security measures can be taken for different departments of a tenant.
In addition, the SD-WAN Solution can connect to a third-party cloud security gateway to protect SaaS service traffic and traffic for accessing public clouds.
How Is SD-WAN Related to Clouds?
In the cloud era, more and more companies are migrating their IT systems to the public cloud. Enterprise WANs also require flexible access to various cloud resources, such as Infrastructure as a Service (IaaS) cloud services and SaaS cloud applications. vCPEs can be deployed as edge nodes in public cloud locations to provide software-based security, WAN acceleration, and load balancing capabilities over VNFs. Integrating these capabilities into the CPE reduces equipment costs and power consumption, and enables flexible and rapid service delivery.
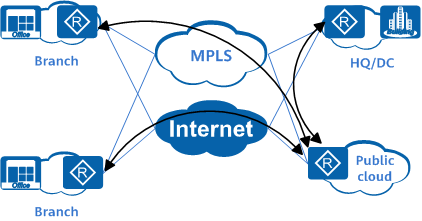 Connecting to a public clouds
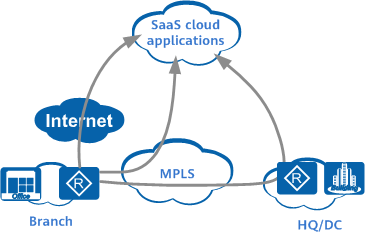
Connecting to a public cloudsMultiple paths to SaaS cloud applications may be available to ensure access efficiency. SD-WAN solutions leverage intelligent traffic control capabilities to understand service level agreements (SLAs) for each available path in real time. SD-WAN solutions can use a centralized network control system to coordinate and select the best path to access SaaS cloud applications in real time.
Categories
Customers
Contact
- Graha Aldiron Blok A No 17-18
- Jalan Daan Mogot no 119, Duri Kepa, Jakarta Barat 11510
- 02129448465 - PT Neotech Cakrawala Indonesia
- admin@neotech.co.id
- 08.30 - 17.30 WIB