Advanced Persistent Threat (APT)
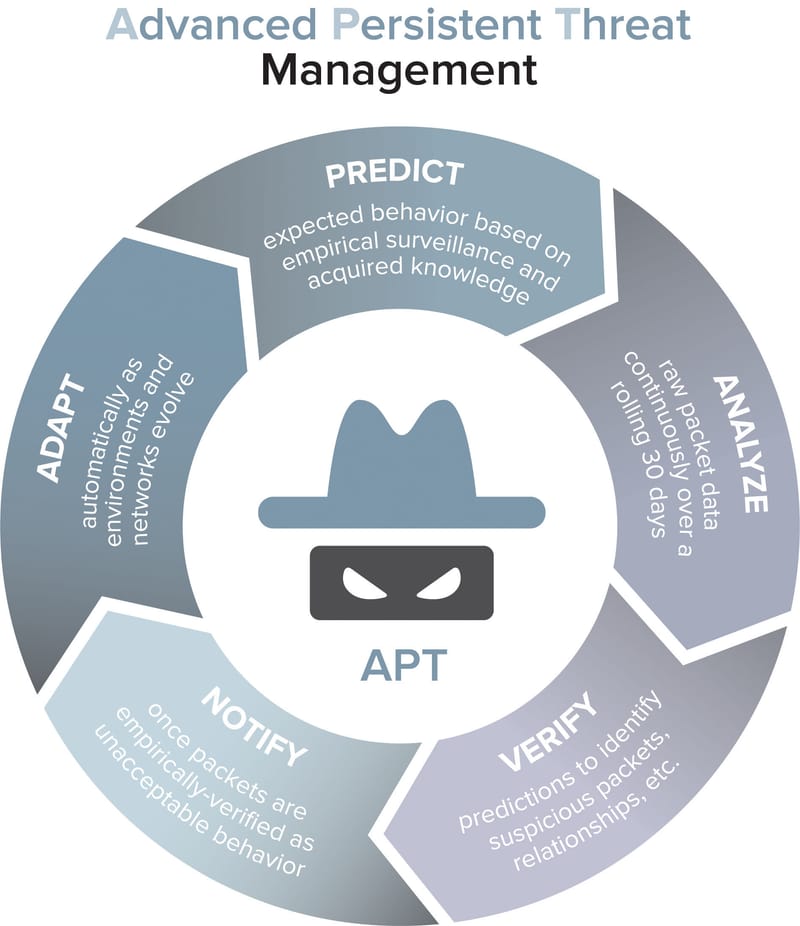
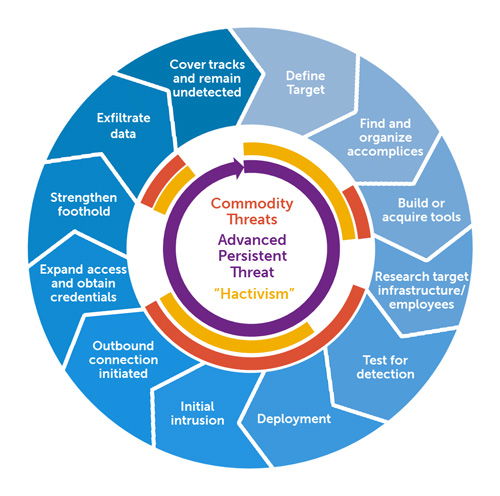
An advanced persistent threat (APT) is a covert cyber attack on a computer network where the attacker gains and maintains unauthorized access to the targeted network and remains undetected for a significant period. During the time between infection and remediation the hacker will often monitor, intercept, and relay information and sensitive data. The intention of an APT is to exfiltrate or steal data rather than cause a network outage, denial of service or infect systems with malware.
APTs often use social engineering tactics or exploit software vulnerabilities in organizations with high value information.
Who would launch an APT attack?
Numerous entities--large and small, public sector and private--can benefit from a successful advanced persistent threat. Many suspect that governments and nation states have used APT attacks to disrupt specific military or intelligence operations. Examples include the Titan Rain, Ghostnet, Stuxnet attacks and others. In addition, smaller groups are using simpler tools, such as social engineering, to gain access and steal intellectual property.
Why would someone launch an APT?
A successful advanced persistent threat can be extremely effective and beneficial to the attacker. For nation states, there are significant political motivations, such as military intelligence. For smaller groups, APTs can lead to significant competitive advantages or lucrative payouts.
How do I prevent an APT?
This is a loaded question. When organizations detect gaps in their security, they intuitively deploy a standalone product to fill that void. A solution filled with standalone products, however, will continue to have inherent gaps.
To avoid these gaps in security, organizations need to take a holistic approach. This requires a multilayered, integrated security solution. Deploying a portfolio of products that can seamlessly work together is the best way to enhance security.


